Peeking through the virtual curtain

A new study from the MLSEC group, chaired by Prof. Dr. Konrad Rieck, at BIFOLD and scientists from TU Braunschweig and TU Wien shows that virtual backgrounds in popular video calling platforms like Zoom and Google Meet do not reliably conceal the user’s physical environment. The study was presented at the 2025 USENIX Security conference in Seattle, USA.
Not least as a consequence of the Covid 19-pandemic, video calls have become an essential part of remote work. They enable employees to collaborate from different locations, including their homes. Transmitting videos from personal space, however, poses a privacy risk: participants may gain insight into private information through details in the background. To limit this risk, video conferencing services implement various virtual backgrounds that conceal the real environment during a video call. Unfortunately, this protection is not flawless, and pixels from the environment occasionally become visible during a video call. But does this really constitute a privacy problem?
Spotting and aggregating imprecision
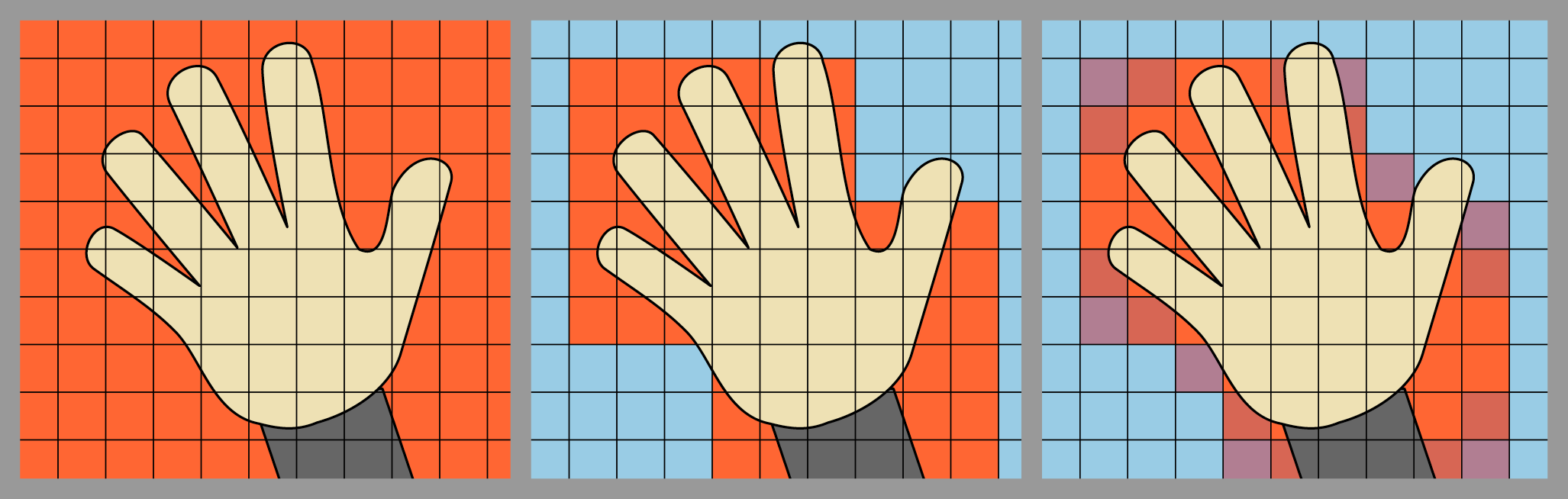
To demonstrate the risk of this threat, the team developed a novel attack that reconstructs users’ surroundings through virtual backgrounds. The idea is simple: pixel leaks arise from the difference between where the virtual background algorithm “thinks” the user is and where they actually are. Since this information is not directly available to an attacker, the researchers devised a method to approximate it by combining high-quality image segmentation with a repurposing of the original video conferencing software. “Even if only a few pixels leak at each moment, over time this is enough to reveal details of the room,” notes Konrad Rieck. In tests, the researchers compared their method with previously published attacks and found that it extracted about 53% more leaked environmental pixels. This, in turn, enabled the reconstruction of larger areas and more recognizable room structures and objects.
„Although virtual backgrounds are widely believed to protect users’ privacy, our study reveals that this perceived safety is often illusory. Unfortunately, at present, it is not clear how an effective and at the same time efficient defense can be constructed. With the advancement of capabilities in mobile devices and desktop computers, this may change in the future. In the meantime, we recommend preparing the room environment carefully to avoid unintentional leaks in video calls“, adds Konrad Rieck.
The publication in detail:
Seeing through: Analyzing and Attacking Virtual Backgrounds in Video Calls
Felix Weißberg, Jan-Malte Hilgefort, Steve Grogorick, Daniel Arp, Thorsten Eisenhofer, Martin Eisemann and Konrad Rieck.
Proc. of the 34th USENIX Security Symposium, 2025.



